
Web 1. Toke Relaunch
Challenge description: We’ve relaunched our famous website, Toke! Hopefully no one will hack it again and take it down like the last time.
Once we access the static webpage we’re presented with a button that does nothing and some text.
Index.html
I had a look at the html and some js files, but found nothing on them. So that’s when I started checking if there were any common files on the web server, like .htaccess, .htpasswd, sitemap.xml or robots.txt. And it turned out there was a robots.txt file present:
1
2
User-agent: *
Disallow: /secret_xhrznylhiubjcdfpzfvejlnth.html
Curl’ing the file present on it (https://static.icec.tf/toke/secret_xhrznylhiubjcdfpzfvejlnth.html) gave us the flag:
IceCTF{what_are_these_robots_doing_here}
Web 2. Lights out
Challenge description: Help! We’re scared of the dark!
Again we get a static webpage, this time with nothing on it, just a question.
Index.html
So let’s inspect the html:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
<!doctype html>
<html>
<head>
<meta charset="utf-8" />
<title>Lights out!</title>
<link rel="stylesheet" href="main.css" />
</head>
<body>
<div class="alert alert-danger">Who turned out the lights?!?!</div>
<summary>
<div class="clearfix">
<i data-hide="true"></i>
<strong data-show="true">
<small></small>
</strong>
<small></small>
</div>
</summary>
</body>
</html>
Apparently there is nothing on it, so I’ll also have a look at the css file. However, I’m going to use Chrome’s inspect, as it lets me have a look at each element separately.
Styles of .clearfix and tags: i, strong and small
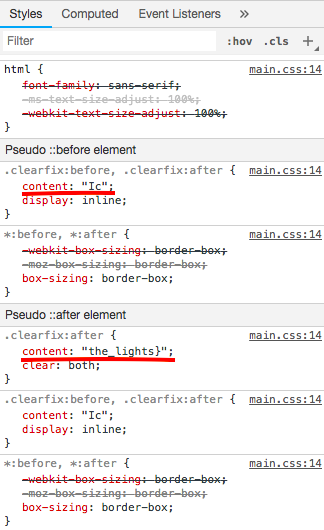
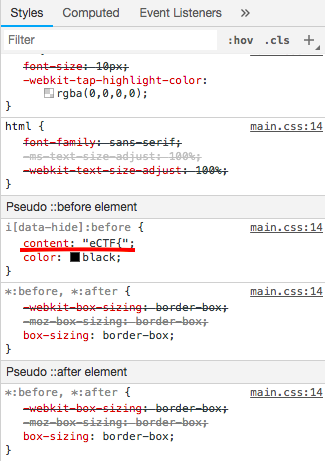
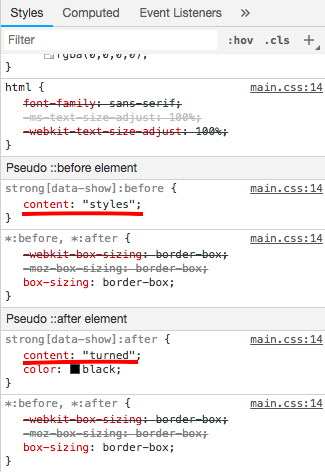
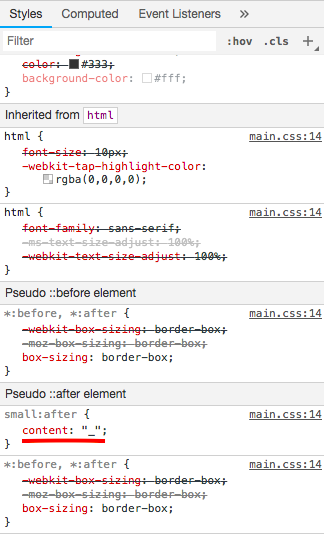
So from there we can reverse the flag and get:
IceCTF{styles_turned_the_lights}
Web 3. Friðfinnur
Challenge description: Eve wants to make the hottest new website for job searching on the market! An avid PHP developer she decided to use the hottest new framework, Laravel! I don’t think she knew how to deploy websites at this scale however….
In this third challenge we get a website which lists jobs available on the market. We can see different pages:
Index.html
Jobs.html
And now inside each job we get some textareas to post data to the server.
Job panel
I spent much time thinking the vulnerability was there, when I accidentally came across an invalid path that threw an exception and, surprisingly, the flag as well:
Debug exception
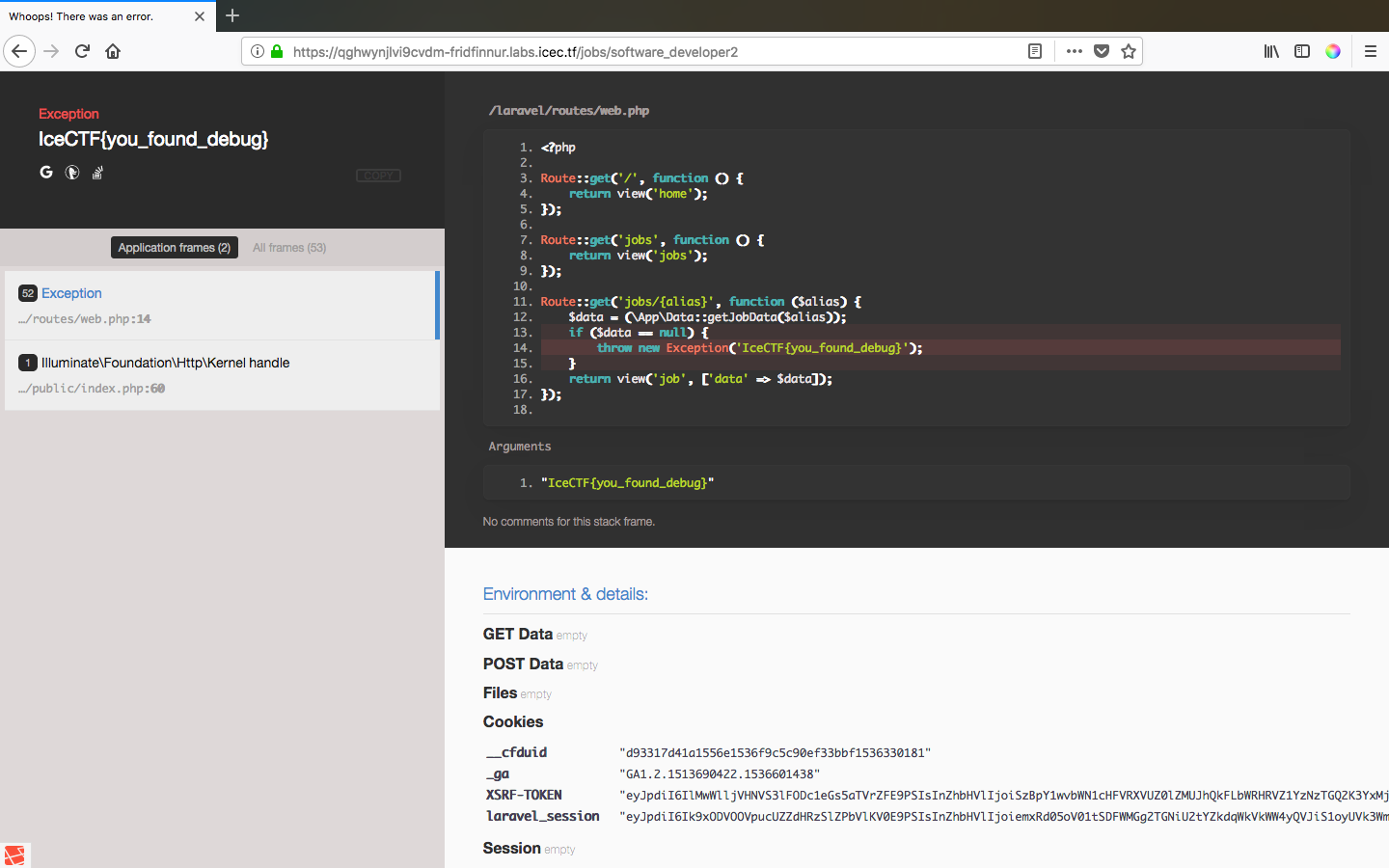
So the flag is IceCTF{you_found_debug}.